CI CD Technology: Build, Test, Deploy Faster

CI/CD technology is no longer “nice DevOps plumbing.” It is the delivery system that determines how quickly your organization can learn, ship, and recover when something breaks. The teams that win in 2026 are not just writing code faster, they are turning small changes into safe production outcomes on repeat.
At a practical level, CI/CD technology is the set of tools and practices that automate what used to be slow, manual, and error-prone: building, testing, packaging, deploying, and verifying software. Done well, it shrinks lead time, reduces change failure rate, and makes deployments routine instead of risky.
What CI/CD technology actually means (and why the terms get mixed up)
CI/CD is often used as a single phrase, but it helps to separate the concepts:
- Continuous Integration (CI): Every change is integrated frequently (ideally daily), validated by automated builds and tests.
- Continuous Delivery: Every change is kept in a deployable state, with automated deployment to non-production and a controlled release to production.
- Continuous Deployment: Every validated change is automatically released to production (no human gate), typically with strong progressive delivery and rollback.
Here is a quick way to align terminology across product, engineering, and compliance stakeholders:
| Practice | What it guarantees | Typical production gate | Best for |
|---|---|---|---|
| Continuous Integration (CI) | Main branch stays buildable and tested | Manual release process | Teams starting automation, legacy systems |
| Continuous Delivery | You can deploy anytime with low risk | Human approval, change window, or automated policy | Regulated environments, critical systems |
| Continuous Deployment | Every green change goes to prod | No human approval, but strong automated controls | High-velocity SaaS, mature incident response |
A useful reference for measuring outcomes is the DORA metrics (deploy frequency, lead time for changes, change failure rate, time to restore). Google’s DORA research popularized these as leading indicators for delivery performance and reliability.
The core building blocks of a modern CI/CD stack
CI/CD technology is a chain. If one link is weak (flaky tests, slow builds, environment drift), the system slows down or becomes untrustworthy.
1) Version control and a delivery-friendly branching strategy
CI/CD starts with how changes flow through Git. Most high-performing teams converge on trunk-based development (short-lived branches, frequent merges) because long-lived branches increase merge risk and delay feedback.
If you are scaling engineering practices, pairing trunk-based development with clear ownership and lightweight governance is usually more effective than adding more approval layers. (Wolf-Tech covers scaling delivery systems in Application Development Roadmap for Growing Teams.)
2) A CI runner that is fast, reproducible, and observable
Your CI platform (GitHub Actions, GitLab CI, CircleCI, Buildkite, Jenkins, etc.) is less important than whether it supports:
- Repeatability (same inputs produce same artifacts)
- Caching (dependencies, build outputs)
- Parallelism (tests and builds run concurrently)
- Good logs and artifacts (easy debugging)
3) Automated testing that is designed for speed and trust
CI/CD technology lives or dies on test signal quality. A slow test suite encourages bypassing. A flaky test suite destroys trust.
A pragmatic target is: fast checks on every commit, deeper checks pre-release, and production verification after release.
If you want a metrics-first approach to test signal and quality, Wolf-Tech’s guide on code quality metrics that matter is a strong companion.
4) Artifact management and immutable builds
High-integrity delivery relies on building once and promoting the same artifact across environments.
Common practices include:
- Container images pushed to a registry
- Versioned packages (npm, Maven, NuGet, PyPI) with a clear publishing policy
- Signed artifacts and provenance metadata for supply-chain assurance
5) Infrastructure as Code (IaC) and environment consistency
If environments drift, deployments become unpredictable. IaC (Terraform, Pulumi, CloudFormation, etc.) helps make environments reproducible, reviewable, and auditable.
For teams modernizing legacy systems without disrupting users, environment consistency is also what makes safer release patterns like canaries and blue/green feasible. (Related: Modernizing Legacy Systems Without Disrupting Business.)
6) Deployment automation plus progressive delivery controls
Deployment is not just “copy files and restart.” Mature CI/CD technology includes:
- Automated deploy orchestration
- Health checks and readiness gates
- Feature flags
- Canary releases and automated rollback
On Kubernetes, GitOps tools like Argo CD or Flux often become the operational backbone for CD because they make desired state explicit and reviewable.
7) Observability and production verification
The pipeline should not end at “deploy succeeded.” It should end at “users are safe.”
That means linking deployments to:
- SLIs/SLOs (latency, error rate, saturation)
- Logs and traces
- Business KPIs (signups, payments, conversion)
A deployment that increases error rate is a failed deployment, even if your CI tool shows a green check.
A reference pipeline: from commit to verified release
Most organizations benefit from a simple reference model that everyone understands, and then iterating.
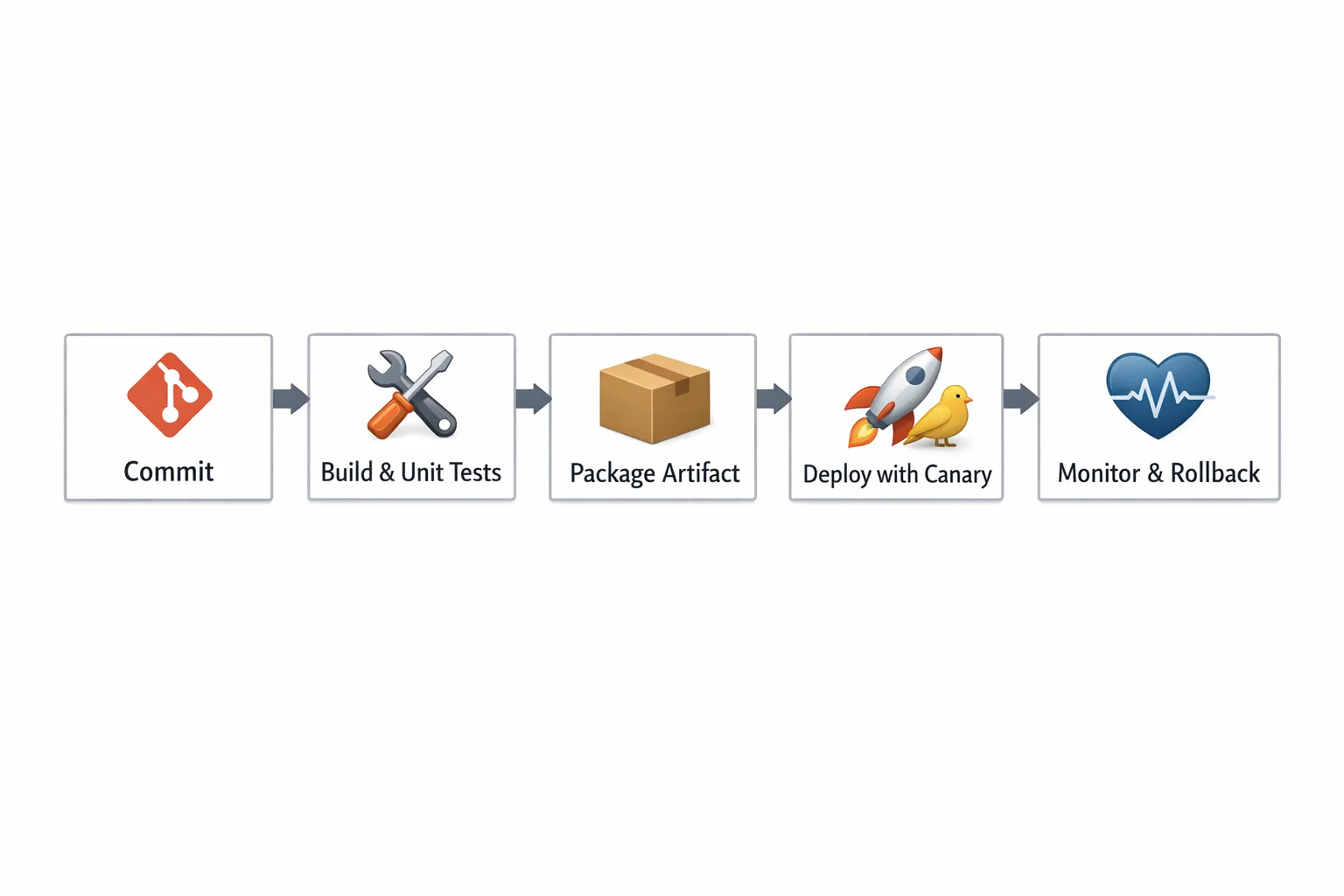
In practice, each stage should answer one question:
- Commit: Is the change small and reviewable?
- Build and unit tests: Does it compile, lint, and pass fast checks?
- Package artifact: Can we promote the same artifact to higher environments?
- Deploy (canary/blue-green): Can we release with controlled blast radius?
- Monitor and rollback: Do we detect harm quickly and revert safely?
This is also where CI/CD technology intersects with reliability engineering. If rollback is manual, slow, or scary, teams will deploy less often, and each deploy becomes bigger and riskier.
Where teams lose speed (and how CI/CD technology fixes it)
Many teams “have CI/CD” but still ship slowly because the pipeline is not optimized for feedback loops. The usual culprits are predictable.
| Bottleneck | What it looks like | High-leverage fix | What to measure |
|---|---|---|---|
| Slow builds | 20 to 60 minute pipelines | Cache dependencies, split jobs, remove wasted work, prebuild images | Median CI duration, p95 CI duration |
| Flaky tests | Reruns and “it passed on my machine” | Quarantine, fix root causes, stabilize timing, add determinism | Flake rate, rerun count |
| Long-lived branches | Painful merges, late surprises | Trunk-based development, smaller PRs, feature flags | PR age, PR size, lead time |
| Manual environment work | “Works in staging only” | IaC, ephemeral preview envs, consistent config | Deployment success rate |
| Risky releases | Big bang deploys, long freeze windows | Canary, blue/green, automated rollback | Change failure rate, MTTR |
A key pattern is to shift feedback left (catch issues earlier) without making early stages slow. That is why most mature pipelines use a layered approach: quick checks for every commit, heavier suites less frequently, and production verification always.
Choosing CI/CD tools without getting locked in
Teams often start by selecting a tool, then trying to build a delivery system around it. A better approach is to decide what guarantees you need (speed, evidence, auditability, rollback), then pick tools that match.
Here is a practical way to evaluate CI/CD technology by category:
| Category | What to look for | Common options (examples) |
|---|---|---|
| CI platform | Caching, parallelism, secrets, good logs, self-hosting option | GitHub Actions, GitLab CI, CircleCI, Jenkins, Buildkite |
| CD / deployment | Declarative deploys, environment promotion, drift detection | Argo CD, Flux, Spinnaker |
| Containers and registry | Immutable images, scanning support, retention policies | Docker + registry (vendor-specific) |
| IaC | Policy support, plan review, modularity | Terraform, Pulumi, CloudFormation |
| Secrets | Rotation, access controls, audit logs | Vault, cloud secret managers |
| Release controls | Flags, targeting, kill switches | Feature flag platforms, custom flags |
If you are already deep into a platform ecosystem, it is usually sensible to lean into it. For example, GitHub Actions plus cloud-native registries and IaC can be a strong baseline. If you are operating at large scale or strict compliance, you may need more explicit separation of duties and richer evidence capture.
Wolf-Tech also maintains a broader tooling perspective in Best Application Development Software for 2025, which includes CI/CD and adjacent systems like observability and security tooling.
CI/CD technology in regulated or high-risk environments
“Move fast” does not mean “skip controls.” In finance, healthcare, and other regulated domains, a modern CI/CD setup is often the best way to improve auditability and reduce human error.
Common patterns that work well:
- Continuous Delivery with controlled promotion: everything is automated up to production, then a policy gate approves release (human or automated).
- Evidence by default: pipeline logs, test results, artifact digests, and approval records are retained and searchable.
- Separation of duties without handoffs: approvals are explicit, but the process is still push-button and repeatable.
Security and supply-chain requirements increasingly show up here. Two useful starting points:
- NIST Secure Software Development Framework (SSDF) for secure development practices and governance
- SLSA (Supply-chain Levels for Software Artifacts) for integrity controls like provenance
In practical terms, this usually means adding steps such as dependency scanning, SBOM generation, artifact signing, and policy enforcement, but only if you can keep feedback fast. If security gates take hours, teams will route around them.
A pragmatic adoption plan (without boiling the ocean)
If you are improving CI/CD technology in an existing organization, the goal is not “install a pipeline.” The goal is to change the economics of shipping so that small, safe releases are the default.
Days 0 to 30: Make the main branch trustworthy
Focus on the minimum set of guarantees:
- CI runs on every change and finishes in a reasonable time
- Build is reproducible and outputs an immutable artifact
- A small, reliable test suite runs fast (plus lint, type checks)
- Basic deployment automation exists for a non-production environment
This is also the moment to tackle the biggest credibility killer: flaky tests.
Days 30 to 60: Make deployments routine
Once CI is stable, invest in CD:
- Infrastructure and environment changes are managed as code
- Deployments are automated, repeatable, and observable
- Rollback is documented and tested
- Preview environments exist for meaningful review (when applicable)
Days 60 to 90 and beyond: Optimize feedback loops and risk controls
Now you can safely add sophistication:
- Canary releases and automated rollback based on SLO signals
- Feature flags for decoupling deploy from release
- Security and supply-chain automation (scanning, SBOM, signing)
- Metrics-driven continuous improvement using DORA metrics
If you are doing this while modernizing legacy code, you will often need a staged approach where CI/CD is introduced per module or service boundary, not across the entire monolith at once. Wolf-Tech’s legacy modernization guidance in Taming Legacy Code: Strategies That Actually Work aligns well with incremental delivery upgrades.

Common pitfalls to avoid
CI/CD technology fails most often for organizational reasons, not tool reasons.
- Treating CI/CD as “DevOps’ job”: delivery is a product capability. App teams must own it.
- Building a giant pipeline before proving value: start with a thin vertical slice and expand.
- Making approvals the only risk control: approvals do not reduce defects, fast feedback and progressive delivery do.
- Ignoring operability: if you cannot observe and rollback, you cannot safely move faster.
If you want a broader systems view of delivery maturity (DevOps, security-by-design, observability, governance), Wolf-Tech’s vendor-oriented checklist in Top Traits of Web Application Development Companies is also a useful internal benchmark for your own team.
Frequently Asked Questions
What is CI/CD technology in simple terms? CI/CD technology is the tooling and automation that takes code from a developer commit through build, test, and deployment, then verifies the release in running environments. The goal is faster feedback and safer releases.
What is the difference between continuous delivery and continuous deployment? Continuous delivery means your software is always in a deployable state and production releases are controlled (often with a gate). Continuous deployment means every change that passes automated checks is released to production automatically.
Do small teams really need CI/CD? Yes. Small teams benefit the most because automation prevents context switching and reduces the cost of mistakes. A lightweight pipeline (build, unit tests, deploy to staging) can pay off quickly.
How do we speed up CI pipelines without reducing quality? Start by measuring build time, then apply caching and parallelism, reduce unnecessary work, and stabilize flaky tests. Keep fast checks on every commit and move heavier suites to pre-release or nightly runs.
Is CI/CD compatible with compliance requirements? Yes. In regulated environments, CI/CD often improves compliance because it produces consistent evidence (test results, artifact hashes, approvals) and reduces manual, error-prone steps.
What metrics should we track to know if CI/CD is working? Track DORA metrics (deploy frequency, lead time, change failure rate, time to restore) plus pipeline-specific metrics like CI duration, flake rate, deployment success rate, and rollback time.
Build, test, and deploy faster with Wolf-Tech
If your releases are slow, risky, or overly manual, the fix is rarely “switch CI tools.” It is usually a delivery-system upgrade that combines pipeline engineering, test strategy, deployment safety patterns, and pragmatic governance.
Wolf-Tech helps teams design and implement CI/CD technology as part of end-to-end delivery, from full-stack development to Cloud and DevOps, legacy code optimization, and code quality consulting. If you want a practical assessment of your current pipeline, bottlenecks, and the fastest path to safer, more frequent releases, reach out via wolf-tech.io.

