Custom Software Application Development: End-to-End Guide

Custom software can be a growth engine or an expensive “maybe.” The difference usually is not talent, it is whether you run custom software application development as an end-to-end system: outcomes and constraints first, architecture and delivery next, then launch, operations, and continuous improvement.
This guide walks through that full lifecycle in a practical way, aimed at CTOs, product leaders, and engineering managers who need software that ships safely, integrates cleanly, and keeps paying off after go-live.
What custom software application development actually covers
“Application development” is broader than a web app. In 2026, many successful custom applications include a mix of:
- A browser UI (internal tools, customer portals, dashboards)
- Mobile clients (field work, consumer experiences)
- Backend services and APIs (business rules, integrations)
- Data stores and analytics (operational reporting, audit trails)
- Identity and authorization (SSO, roles, tenancy)
- Cloud and DevOps (CI/CD, monitoring, incident response)
So the job is not “build features,” it is to deliver a reliable, secure product capability that can evolve.
A useful working definition:
Custom software application development = discovering the right outcome, designing the right user and system flows, implementing them with quality gates, shipping to production safely, and operating with measurable reliability and cost controls.
Phase 0: Confirm you should build (and what to keep out of scope)
Before discovery, make one decision explicitly: build, buy, or hybrid.
Many teams skip this because they “already decided.” But when the real costs show up (integrations, compliance, data migration, change management), re-litigating the decision mid-project becomes painful.
| Option | When it tends to win | Common pitfalls to plan for |
|---|---|---|
| Buy SaaS | Commodity workflows, fast time-to-value, strong vendor roadmap | Vendor lock-in, limited customization, data export limits, integration constraints |
| Build custom | Differentiated workflows, complex domain rules, unique integrations, competitive advantage | Underestimating operability, security, long-term ownership, unclear requirements |
| Hybrid (compose/wrap) | You want SaaS for core and custom for differentiation, orchestration, UX | Integration complexity, identity/permissions mismatch, duplicated data |
If you want a deeper decision framework, Wolf-Tech covers it in When to Choose Custom Solutions Over Off-the-Shelf.
Phase 1: Discovery that produces buildable truth (not slides)
Discovery is where teams either buy certainty or accumulate risk.
A strong discovery phase outputs decisions and artifacts that engineering can execute, not just a feature wishlist. A good baseline is:
- Outcome brief (who, what job, measurable success)
- Scope boundaries (explicitly what is not included)
- Critical workflows (happy path plus failure paths)
- Constraints (compliance, hosting, latency, data residency)
- Non-functional requirements (availability, performance, change safety)
- Integration map (systems of record, APIs, files, manual steps)
- Top risks with a mitigation plan (build spikes, vendor calls, prototypes)
A pragmatic pattern Wolf-Tech frequently recommends across guides is the thin vertical slice: one end-to-end path that touches UI, API, data, auth, and deployment early, so you learn reality fast (not in month four). Their broader delivery flow is outlined in Software Building: A Practical Process for Busy Teams.
Discovery mistake to avoid: “Requirements are done”
In custom software, requirements are never “done,” they get progressively validated. The goal is to reduce uncertainty in the riskiest areas first (integrations, permissions, data correctness, performance constraints).
Phase 2: Design the product and UX for real-world constraints
Design is where many custom applications fail quietly, because teams design screens but not the system behavior around them.
To keep the design buildable and reliable, make sure UX work includes:
- Roles and permissions (who can do what, including admins and support)
- Error states and recovery (timeouts, partial failures, retries)
- Auditability needs (what must be logged, exported, retained)
- Data validation rules (at input time and at write time)
- Accessibility expectations (at least WCAG-aligned basics for enterprise)
- Empty states and onboarding (first-run success is adoption)
Wolf-Tech’s end-to-end design workflow, including artifacts that engineering can implement directly, is detailed in Software Designing: From Requirements to UI Flows.
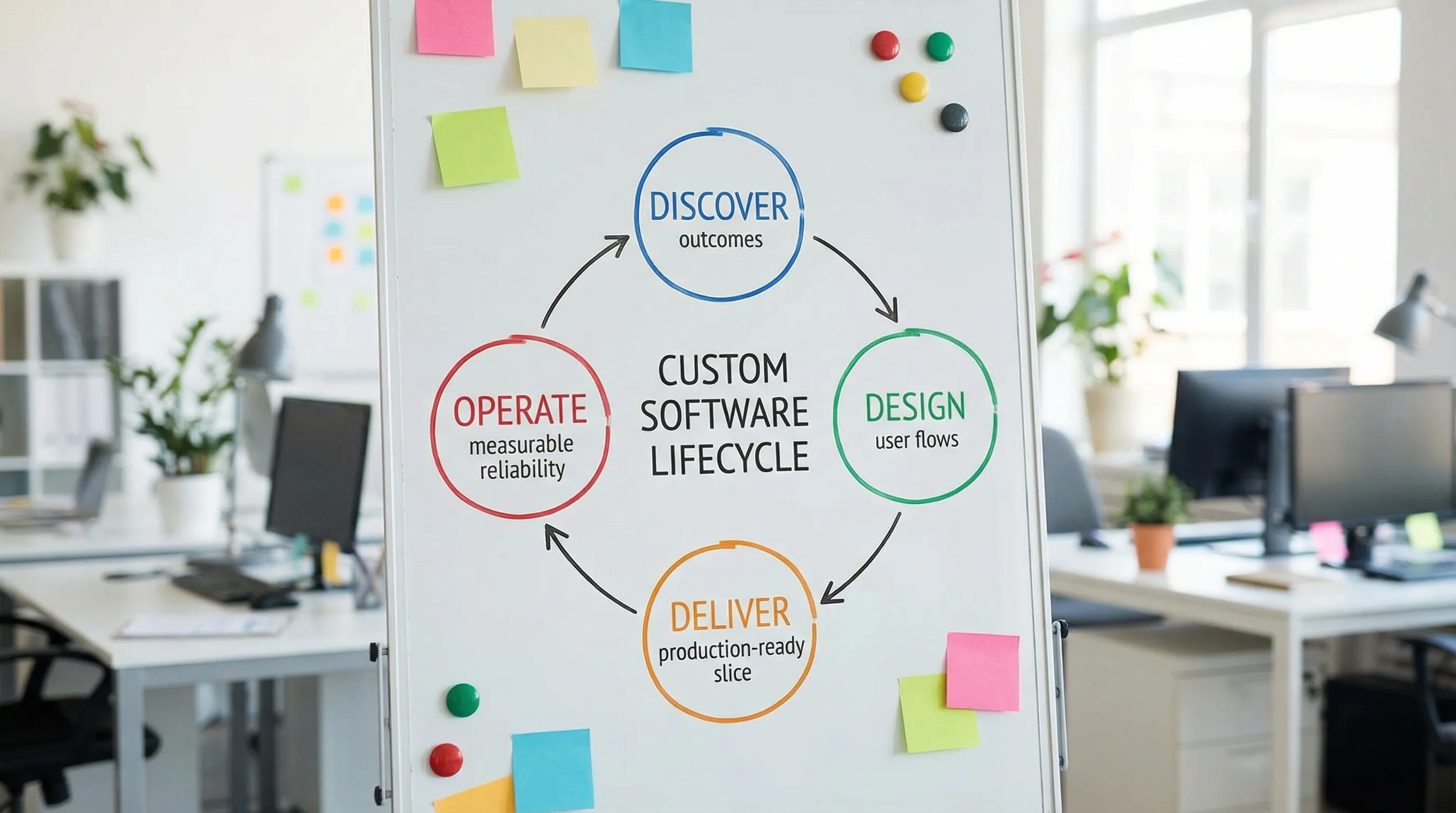
Phase 3: Architecture and tech stack decisions that reduce long-term cost
Architecture is not about picking trendy components. It is about setting a baseline that matches:
- Domain complexity
- Team size and skills
- Reliability and security requirements
- Deployment and data constraints
- Expected change rate
For many products, the best starting point is a modular monolith (clear internal boundaries, one deployable unit). It often yields faster iteration and simpler operations early, while still supporting later extraction when boundaries become stable.
The “minimum viable architecture” decisions
Even for an MVP, you need a few decisions early because they are expensive to reverse:
- Identity approach (SSO, OAuth/OIDC, tenant model)
- Data ownership and lifecycle (source of truth, retention, deletion)
- Integration strategy (sync vs async, events vs APIs)
- Environment strategy (dev, staging, prod, preview)
- Observability baseline (logs, metrics, tracing, alerting)
If you need a practical selection method rather than opinions, Wolf-Tech’s How to Choose the Right Tech Stack in 2025 lays out a scorecard-driven approach that still applies well in 2026.
And if you are inheriting a messy architecture, What a Tech Expert Reviews in Your Architecture is a useful checklist for identifying mismatches between goals and design.
Phase 4: Implementation with quality gates (the delivery system matters)
Custom applications succeed when delivery is a repeatable system, not heroics.
A production-grade implementation phase typically includes:
- Repository and branching model (often trunk-based for speed and safety)
- CI that runs tests and checks on every change
- CD that can deploy safely with a small blast radius
- Local developer experience that reduces cycle time
- Consistent environments and infrastructure automation
Wolf-Tech’s practical guide to pipelines is CI CD Technology: Build, Test, Deploy Faster.
Quality gates you should be able to prove
The point of quality gates is not bureaucracy, it is reducing the cost of defects and making change safe.
| Quality gate | What it prevents | Evidence to expect |
|---|---|---|
| Automated tests (unit + integration) | Regression, brittle refactors | CI pass rate, meaningful coverage, low flake rate |
| Code review with standards | Inconsistent patterns, hidden risk | Review checklist, PR size discipline |
| Static analysis and formatting | “Death by a thousand cuts” maintainability | Lint rules, formatter enforcement |
| Dependency and secret scanning | Supply chain risk, credential leaks | Alerts in CI, patched vulnerabilities |
| Performance budgets (where relevant) | Slow creep that becomes outages | Measured p95, web vitals, load tests |
For metrics that are actually actionable (not vanity dashboards), see Code Quality Metrics That Matter.
Phase 5: Security and compliance by design (not a final-week scramble)
Security work that starts after development is mostly rework.
Even outside regulated industries, modern custom applications typically need:
- Strong authentication and authorization (including tenant isolation)
- Secure handling of secrets and keys
- Input validation and safe data access patterns
- Audit logging for sensitive actions
- A secure software supply chain (dependencies, builds, provenance)
Two widely referenced baselines you can use to structure security requirements and evidence are:
- NIST Secure Software Development Framework (SSDF), SP 800-218
- OWASP Application Security Verification Standard (ASVS)
For threat patterns and common application issues, the OWASP Top 10 remains a practical reference for prioritizing protections.
Phase 6: Data, APIs, and integrations (where timelines often slip)
Integrations are frequently the longest pole in custom application delivery because they involve external constraints: other teams, vendor rate limits, unclear ownership, brittle legacy endpoints, and data quality.
A few integration practices that reduce surprises:
- Define system-of-record ownership per entity (avoid dual truths)
- Use contract tests for critical APIs (consumer-driven or schema-based)
- Version APIs explicitly and set deprecation rules
- Treat data migration as a product problem (validation, reconciliation, rollback)
- Prefer idempotent writes and well-defined retries
If GraphQL is on the table, it can be excellent for complex client needs, but it introduces new operational risks (authorization, query cost, caching). Wolf-Tech’s GraphQL APIs: Benefits, Pitfalls, and Use Cases covers realistic trade-offs.
Phase 7: Launch and operations (where your real costs begin)
Many teams treat launch as the finish line. Operationally, it is the start.
A production launch readiness checklist should include at minimum:
- SLOs and alerting tied to user impact (not CPU graphs)
- Error handling, timeouts, and backpressure
- Backups and restore tests (prove you can recover)
- Runbooks for likely incidents
- Access controls and operational audit logs
- A rollback strategy (feature flags, canaries, blue/green)
Wolf-Tech’s reliability patterns and operational practices are covered in Backend Development Best Practices for Reliability. For broader scaling guidance (including operability and economics), see Developing Software Solutions That Actually Scale.
Phase 8: Iterate, modernize, and scale without rewriting
If you deliver value, change requests follow. Your architecture and delivery system must handle that without slowing down every quarter.
A sustainable post-launch approach typically includes:
- A measured technical debt budget (tied to outcomes like lead time and defect escape)
- Regular refactoring of hotspots, not cosmetic rewrites
- Modularization and boundary hardening as the team grows
- Incremental modernization plans for legacy dependencies
When you do need to modernize, aim for low-risk incremental patterns rather than big-bang rewrites. Wolf-Tech’s Code Modernization Techniques: Revitalizing Legacy Systems is a practical starting point.
Team model and governance: how successful custom apps actually get built
Even strong engineers struggle without clear ownership and decision rights.
A pragmatic setup for custom software application development usually includes:
- A product owner (outcome and scope decisions)
- A tech lead/architect (architecture baseline and change safety)
- Full-stack engineers (end-to-end delivery)
- QA or quality ownership (automation focus, release confidence)
- DevOps/platform capabilities (pipeline, environments, observability)
- Security support (threat modeling, SDLC controls, reviews)
On governance, two practices work well without heavy process:
- Weekly outcome and risk review (what did we learn, what moved, what is blocked)
- “Definition of Done” that includes operability and security, not just feature completion
If you are selecting a partner, avoid marketing checklists and ask for proofs. Wolf-Tech’s How to Vet Custom Software Development Companies provides an evidence-based scoring approach.
Estimating timelines and budgets without lying to yourself
Custom software estimates are usually wrong for predictable reasons. The biggest drivers are rarely “number of screens.” They are:
- Integration count and quality (unknown APIs, legacy constraints)
- Data migration complexity (reconciliation, audit needs)
- Security and compliance requirements
- Non-functional requirements (availability, performance, change safety)
- Team topology and delivery maturity (CI/CD, test automation, ops readiness)
A reliable way to estimate early is to fund a short phase that produces real evidence (prototype, thin slice, integration spikes) and then re-forecast with measured throughput.
For a structured view of cost drivers and ROI framing, see Wolf-Tech’s Custom Software Development: Cost, Timeline, ROI.
How Wolf-Tech can help
Wolf-Tech works across the full lifecycle, from discovery and tech stack strategy to full-stack implementation, modernization, and code quality consulting. If you need an end-to-end partner or an independent expert to de-risk the plan, start with a small, evidence-driven engagement (for example, architecture review, delivery assessment, or a thin vertical slice plan) and build from there.
Explore Wolf-Tech’s services at wolf-tech.io and use the guides above to align your team on a build process that stays fast, safe, and sustainable.

